Unfortunately, the governments also an enormous obstacle in eliminating the evil. Are but as governments their views from time to time deign to enforce with whatever designed, you are also of the opinion that the citizens could propel not free trade abroad with such technologies, because the potential adversaries may be of use. A completely new procedure that is directed against the government crime in relation to data protection therefore always runs the risk of a trade restriction to be occupied, so that it is no longer reasonably usable for the global community.
In Germany was a big initiative of large email providers to transfer the e-mails only with a transport encryption. But I know from personal experience that has drawn an enormous amount of support by this simple modification.
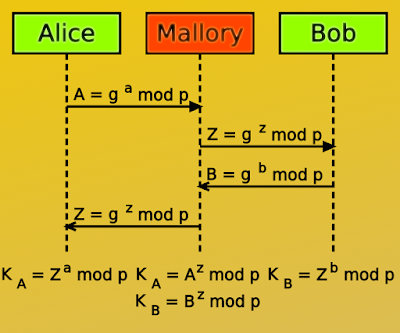
When it comes to eavesdrop just to the passive, there is the Diffi-Hellman key exchange is already the ideal method. If you include this in the TCP / IP stack by way of a TCP / IP option, then would all be based on simple listening activities at a stroke fell. Why is this process so then imposed in the shadows? This is because the basic task than did the science of cryptography to safely transport a very concrete message from Alice to Bob. The evil Mallory can but engage in the connection, then the procedure is null and void:
Installation costs for encryption
What to consider when installing? Nothing! the new kernel can be imported as a security update. Solely the processing power for an application would rise. Since this is but also managed by operating system, it knew in which exceptions a shutdown of encryption is absolutely necessary. Embed this maintenance-free in the production is what I mean when I speak about mass-compatible encryption.Is it possible to detect systematic interception?
Since there is no code widely used for this process here are my suggestion: The use of TLS. TLS solves nearly all known encryption problems. Also Snowden has no evidence supplied that all TLS method are infiltrated by the NSA. Especially as Chipher different countries are installed in the TLS. (USA, Russia, Japan, South Korea). TLS has a weak point. But this is common with al encryption algorithm ih relation to https. You can observe the size to the transferred Data files. This is enough in case of public Avail Documents. The sizes of the Files are Significant for the leaded page in nearly every case. But TLS has the distinct legal advantage that there everywhere public accessible algorithms and much SSL / TLS Internet transmissions are available.The kernel generates at boot his self-signed certificate and private key can be protected with the MMU in a best possible way. No user space application somehow gained access to it. The key should be in the Ram and is gone forever after turning the computer off or every 24 hours when the System recreating one new certificate. So then all Chipher at least have delayed Perfect Forward Security. This is important if we want to prefer hardware encryption components. For inbound connections a data record with IP, destination port and fingerprint of the presented public key is stored in the system log file. If the TCP option is ignored and there is a normal connection was so a special fingerprint like 00:00:00 ... 00:00 is used in the logfile.
This data will be collected and sent by regular https securely encrypted at regular intervals to a group of central agencies, who evaluate the data statistically. Interceptions are characterized by seeing different Fingerprints from different locations, because an interceptor never catches every connection. If certain connections are Intercepted, for example, the port 80 by an anti-virus and cache firewall, then this instance diagnose such Firewall Cache, and generate understandable communiques. Sometimes one wants or do you also have a traffic control. This may also apply to entire nations, only the governments then have always made responsible in the future in public. And if highwaymen as the British still can sell cable capacity itself will show. The Provider will use such routes can not fail to configure a VPN tunnel.
Also important will be, the process is distinguished by the important fact that tools like wireshark can rebuild so that it continue to work with entanglement. The debug with conventional encryption is annoying because slightest error affect that nothing works. If you get no sensible error message - and anyone who has more to do with computers knows how bad they are often - then it is bad when the communication can no longer observed. I often need to hear from decision-makers in business, they don't wanted to have any cryptographic algorithms, because of - not without reason - fear about loss of production.
Extension 31.05: Unfortunate, i cant submit a respond to a comment on the comment system. No Idea why.
If you using DNS Key, the users must take some action to get encrypted connection. And if you must take actions, you can make some mistakes. As result from such mistakes, the connections are no longer possible. You have no Idea about the fear of Manager about production interruption of every kind. A basic encryption against mass spying must work with the same reliability of TCP/IP itself to get the necessary complaining. That this Procedure is an TCP/IP option will ensure, that there are no trouble with old unsupported operation system.
Every Operating system who swaps out to hard disk have also an options to disable the swap out of kernel code. If such an option is not present, the software can swap out hard disk load routine out to the hard disk. This condition will freeze the Operation because reloading will lock in an infinite loop. Load X -> (*) Need load code -> not present -> go back to (*)
Here i talking about avoid spying by copy of data. I am also Talking about detection of mass intercepting. You are right, a reboot will create an new key in my scenario. This looks like a interception of every connection to this computer. This is not a relevant scenario in relation of protection against Organisations like NSA. This technique not encryption to keep one message not disclosed. If you are government of a computer user, you can get gain control of this Computer. This gives you access to everything what happen on this Computer. But if you are away from an computer, interception will change the key only at a peace of the connection. This will detected by statistical analysis from every instance of the control monitors.
TLS ist very well, but it needs costly and critical service intervention. As result it fail against mass spying.